Scammers Target Users of Popular Todo App on Google
I recently came across a developer on X (twitter) who stumbled onto a phishing website that looked exactly like a popular todolist app. This phishing tactic is difficult to catch even if you are technically savvy.

I recently came across a developer on X (twitter) who ran into a phishing website that was advertised on Google. This phishing tactic is difficult to catch even if you are technically savvy.
Here's the background on what happened:
He searched for the well-known Todolist app "todoist" on Google and clicked the first sponsored result, which had the correct logo and URL in the sponsored listing:
But the actual website he was directed to was a lookalike domain and not actually the official todoist website.
If you just glanced at the URL, you might not pick up on the fact that the URL is toidollst.com and not todoist.com. The landing page is similar to what you would expect to see and the logo is the same.
Unfortunately, the developer ended up downloading the software that this phishing website was advertising.
How the Scams works
Phishing websites commonly use pay-per-click ads on search engines and social media platforms. Just like we saw with the Buybuybay facebook ads scam , we're less likely to scrutinize a website that is advertised on one of these platforms. The assumption is that the publisher would prevent scam websites from advertising in the first place. However, that's often not the case.
In the case of this exploit, scams that leverage Google search ads are extra hard to catch since the display URL does not have to match the URL that you are redirected to after clicking the ad.
Scammers will usually register a new domains for each scam to bypass threat intelligence feeds, which classify malicious domains. By the time the domain is classified by these services, the damage is already done.
Handling these Scams
If you happened to click on a sponsored ad that was promoting a lookalike phishing website, you'd have to carefully examine the URL to figure out if you were on a legitimate website. This just isn't practical because we naturally aren't on "high-alert" constantly.
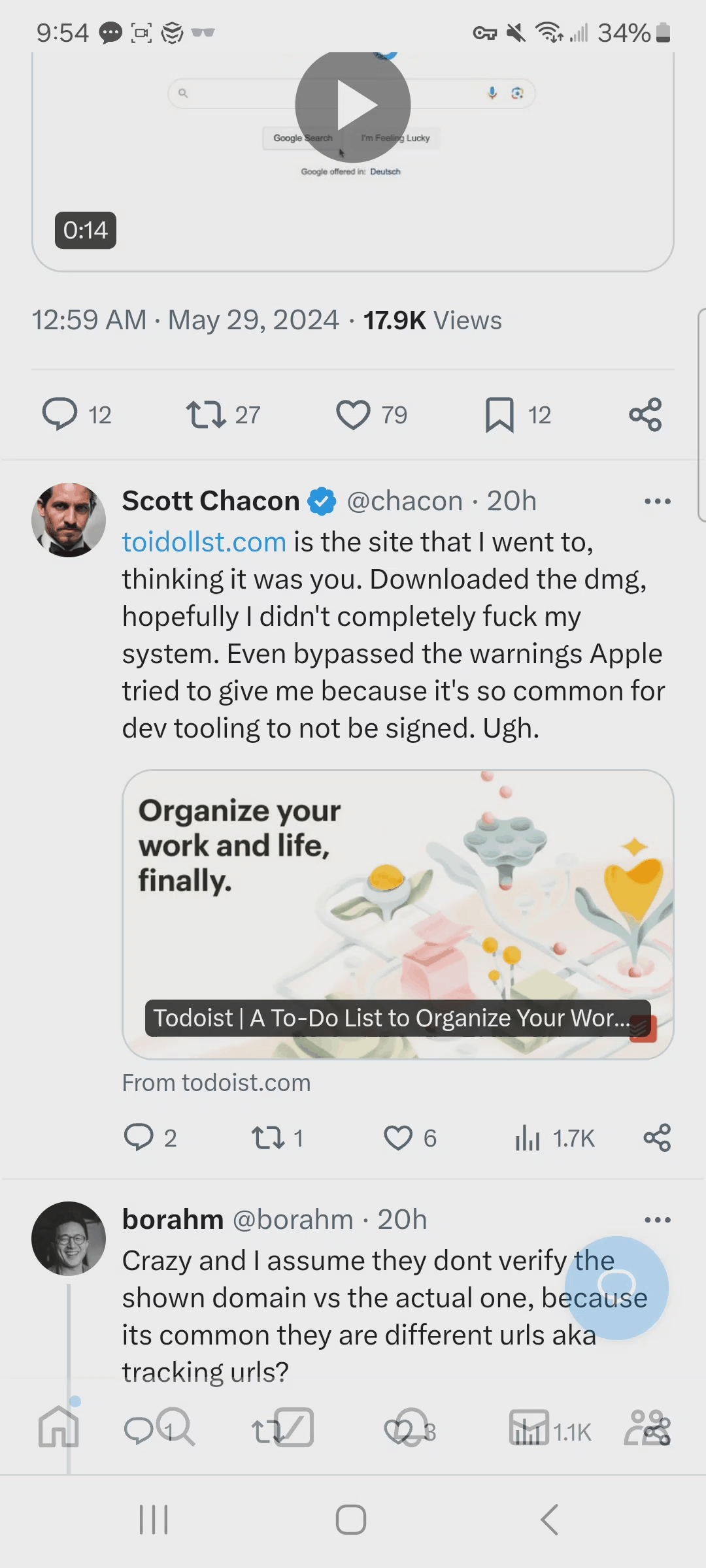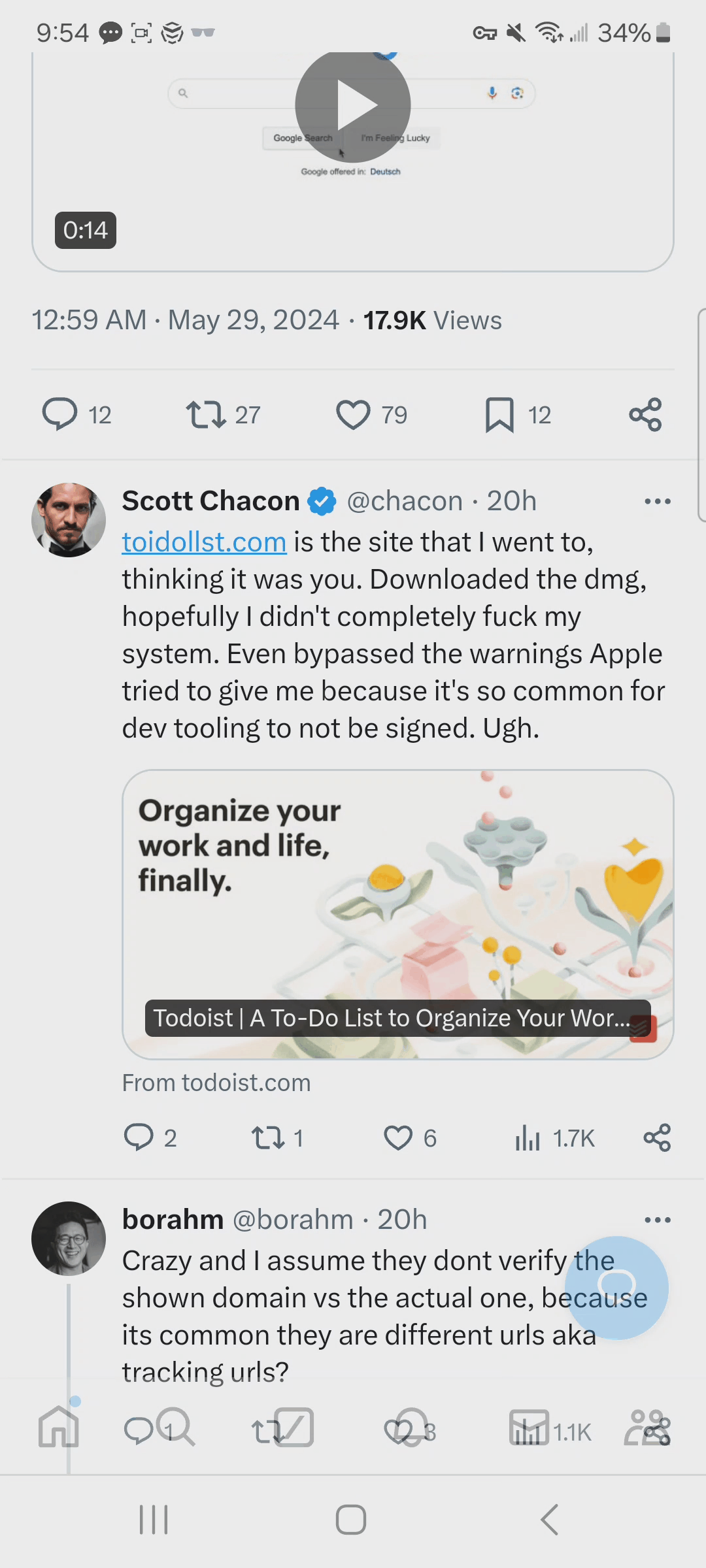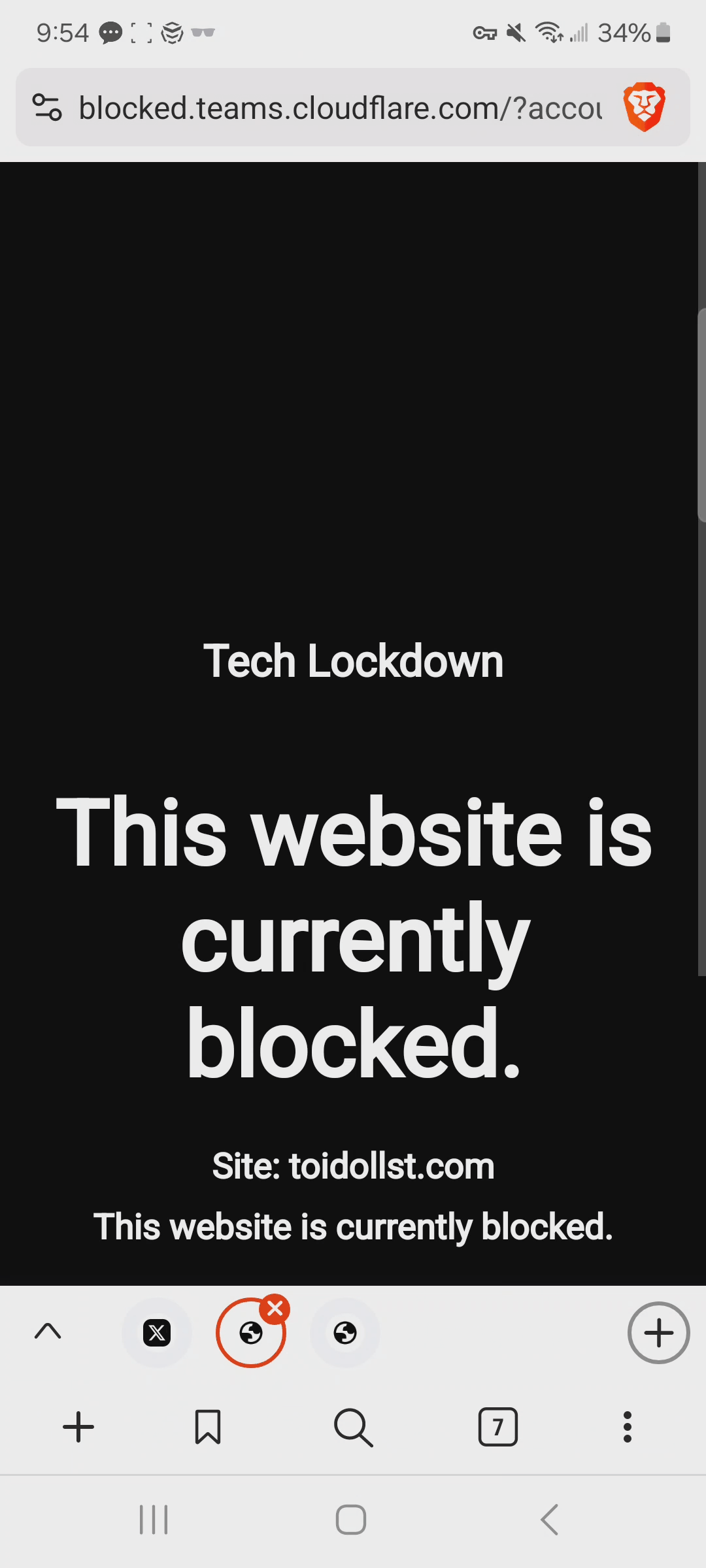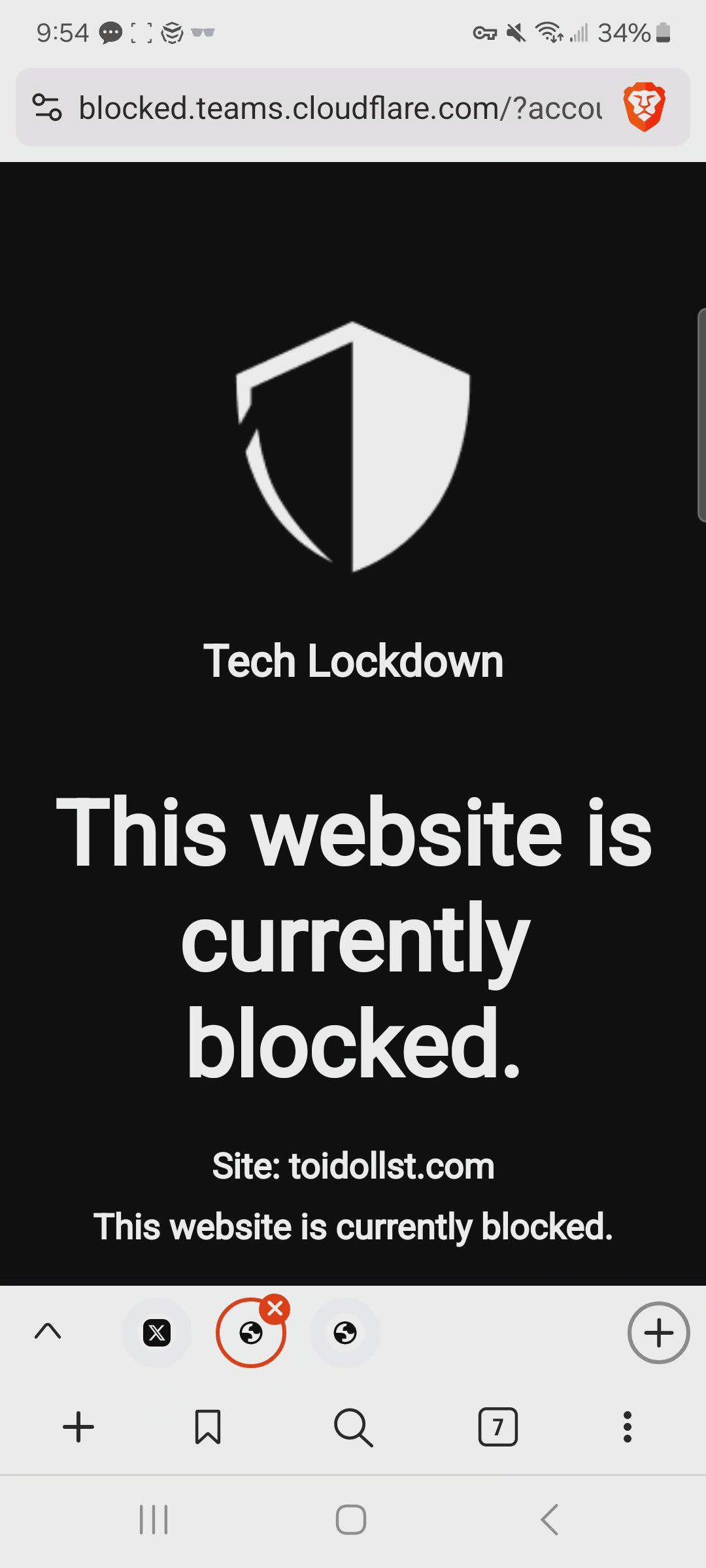
In my case, I went to the phishing link mentioned in the X post and noticed that it was blocked by my DNS Content Policy.
But if you look up the categorization in Cloudflare radar , it's not categorized as a phishing website.
So since this website slipped through the cracks of most threat intelligence feeds, why was it blocked for me?
In my Content Policy , I use the Security Threats preset to block many different types of potential security threats.
The particular threat in this case was Newly Seen Domains. If you click an ad and you land on a website that is categorized this way, there's a good chance it's associated with a scam. These websites are classified this way because they recently published online.
If you are a Tech Lockdown member, make sure your Content Policy has the Security Threats preset added. You can create a new rule and find this under the presets tab.